Setting up LDAP authentication in vFabric Hyperic might be tricky for someone who’s not too familiar with LDAP before as the default values in the vFabric Hyperic settings aren’t exactly useful and the manual doesn’t provide any information on how to get what you need. So here’s a quick tutorial on how to set up LDAP authentication on vFabric Hyperic. The guide works at least with versions 4.6 and 5.7.x as the configuration is the same. The team working on hyperic could have done this a lot simpler but it seems they are just lazy or just don’t have the time.
The original VMware guide can be found here.
- Click HQ Server Settings on the Administration tab.
- Scroll down to LDAP Configuration Properties
- Enable LDAP authentication by checking the box
Now we need to fill in the information
- URL: your forest can be entered here if you want to use any domain controller, for example yourdomain.local. Alternatively you can use the FQDN of you AD server or the IP-address if you want to use one DC specifically
- Username: If anonymous authentication is not allowed, you need to specify a user. You can’t use the UPN nor the pre-windows2000 style username. Instaed you need to specify the distinguishedName value of the user account which includes the distinguishedName, organizational unit and domain. for example CN=hyperic,OU=Users,DC=yourdomain,DC=local
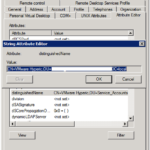
- To find out a users distinguishedName you need to enable advanced options in Active Directory Users and Computers (ADUC) from View -> Advanced Features
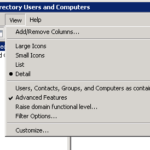
- Select Properties of a user
- Select Attribute Editor tab
- Scroll down to distinguishedName and click view
- Copy the distinguishedName value and click cancel
- To find out a users distinguishedName you need to enable advanced options in Active Directory Users and Computers (ADUC) from View -> Advanced Features
- Password: the password of user account specified previously
- Search Base: If you want to specify a specific Organizational Unit to have access to the Hyperic Server, specify it here. The search base (Organizational unit distinguishedName) can be found similarly to the users distinguishedName from the OUs attribute editor tab. If you want to allow anyone in your AD to log on, specify the domain here in example DC=yourdomain,DC=local
- Search Filter: This can be used to narrow down the search even further for example by using the users location value: (!(location=LOCATIONHERE*))
- Login Property: This specifies how the username should be written in the authentication window. The default cn is not a good idea so change this to sAMAccountName or userPrincipalName
- Optional: set the group search parameters if you want to only allow users who are member of a specific group in AD.
Save the settings and try out to see if your LDAP user account works. If it doesn’t, you will most likely get an error message which might seem cryptic at first. Common error codes are as following:
525 user not found
52e invalid credentials
530 not permitted to logon at this time
531 not permitted to logon at this workstation
532 password expired
533 account disabled
701 account expired
773 user must reset password
775 user account locked
If you are unable to log in, just uncheck “Use my organization authentication” and use your regular login information to get back in. This is by default hqadmin in Hyperic. The first time a user successfully logs in to Hyperic using a LDAP account, a manditory screen will follow asking for the First Name, Last Name, e-Mail address and so on. This is just lazy coding not to populate the default values here from the LDAP query. A user will not get any rights by default, so remember to add your own account to the Super User group to make system wide changes to hyperic.
This guide applies to vFabric Hyperic 4.6 and 5.7. The settings might apply to other versions as well.


Thanks for this information. Unfortunately this is still the same in version 5.8.4. Ridiculous how this process still isn’t described properly!!